How to Hack Line Message

LINE is the world’s most innovative and rapidly increasing mobile messaging app that takes users closer to their loved ones, friends, and families. Since its introduction in 2011, It has over 199 million users all around the globe. It’s a messaging application similar to WhatsApp, Messenger, Viber, etc., allowing users to share photos & videos, Free messaging, Free video & voice calls, etc. You may have a question, Is hacking LINE apps and reading other LINE messages is even possible? Yes, of course, we can hack line messages. Ideas regarding line message hacking are described well below.
In terms of the number of registered users who actively use the app, Line successfully has taken on many other applications such as Skype.
What is Hacking and Its types?
Hacking is an illegitimate operation that is carried out to intrude into someone else’s personal data space to use it for harmful and malicious purposes. There are three types of hackers such as:

White Hat Hackers
It’s generally referred to as Ethical Hacking and is mainly done for good. The main motive of White Hat Hacker is to perform penetration and risk testing. They perform such tasks to find threats and security vulnerabilities of the system only.
Ethical Hacking is a legal process of hacking. A white-hat hacker may purposely try to break a system to find weak points fixed with approval from its owner. For penetration testing and risk tests, many business organizations hire ethical hackers.
Black Hat Hackers
It’s an illegal process of hacking which is also known as Unethical Hacking. When a black hat hacker finds a loophole, they can take advantage of the bug for illegal reasons in a piece of software. They can build an exploit to get inside a computer system to distribute malware, a software tool used to manipulate a given vulnerability to a target user.
Unethical Hacking is an illegal act. This type of hacker has the main motive to achieve personal advantages by stealing private corporate documents, phishing scams, stealing assets from an online bank account, hacking social media, and breaching privacy, etc.
Grey Hat Hackers
It’s the mixture or combination of both black and white hat hackers. Hackers intended to find flaws or mistakes in any devices without the owner’s approval. They can also hack other devices or can find vulnerabilities for their research purpose. Hackers find the error or bug first and report it to the owner later on.
Grey hat hackers prefer first hacking and then seeking permission instead of ethical hackers who get permission earlier. Their goal is to put the insecurity to the owners’ attention and gain the owners’ gratitude or a little bounty.
Is hacking legal?
Ethical hacking is not an illegal operation. It is technically recognized hacking and is not an offense. Until breaking into networks, hackers have approval from their targets, and they are obliged to reveal any bugs they discover. Security hacking is illegal outside of this setting. The Hacker shouldn’t contradict such legal activities: –
- Research and intelligence gathering
- Political purpose
- Professional penetration testing
- Monitoring the children and office employee
- Its legal terms and conditions
Today, more than ever, it has become necessary for businesses and governments to legitimately hack to find and resolve vulnerabilities and avoid malicious and illegal hacking from keeping sensitive information secure.
But once you hack without express permission, it crosses the line from legitimate activity to illegal cybercrime.
Can we Intercept Line Messages?
Technology has progressed to such a dimension where nothing is impossible for a human being. The growth of technologies in every aspect has made people’s life easier. There is also the probability of threats and vulnerabilities on the internet with the rise of new technology. With the aid of specific online hacking instruments and software, line messages can also be intercepted very quickly.
There are many methods and software for hacking Line account. Many software can provide a person with access to read messages of the target device sent using the Line app. You might be curious if hacking LINE apps and reading other LINE messages; photos are even possible. Yes, it’s possible to show some relevant tools and techniques to spy line activities.
Ways to Hack Line Messages
We typically refer to using third-party spy apps when we address the viable way of hacking a LINE account. Using the phone spy application makes hacking someone’s line messages quite easy.
Hack someone’s Line message using MxSpy
MxSpy is the first solution that many users consider as the best Line hack app. This is the ultimate surveillance software with many powerful features for tracking cellular behavior. One of the qualities is to spy on online messages without knowing the target devices.
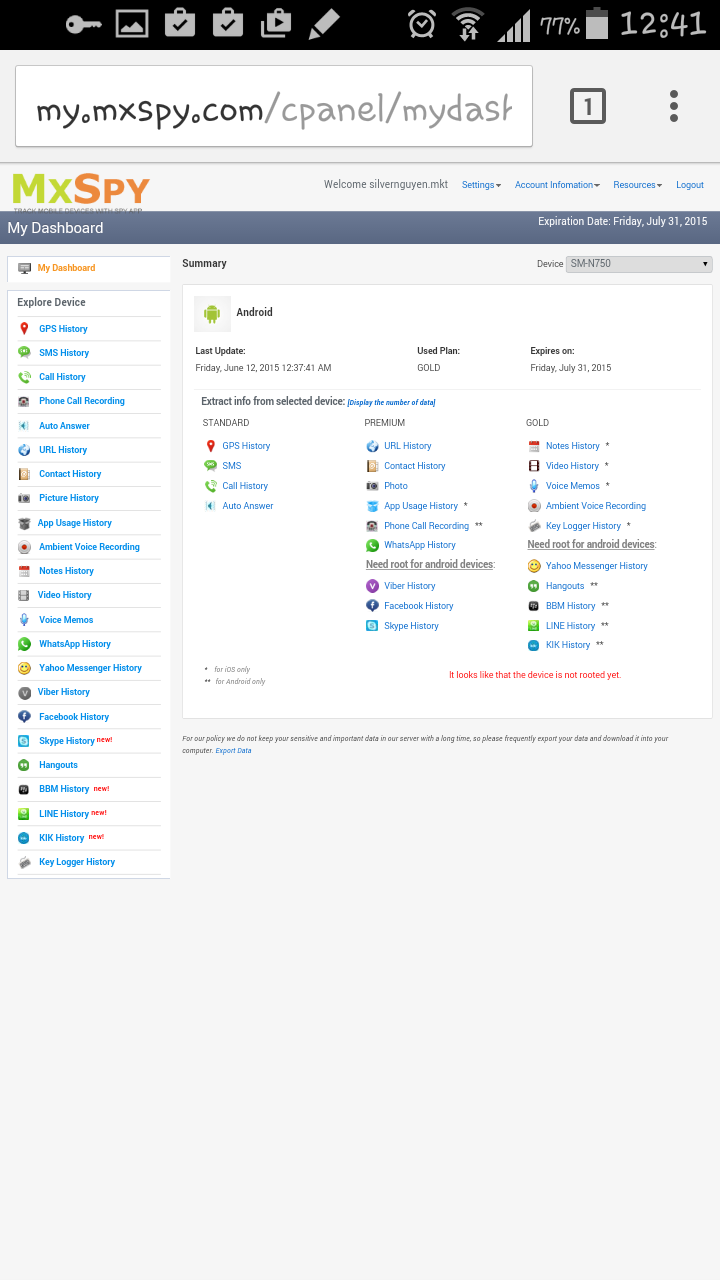
Features
- Limiting incoming calls
- See all the hidden photos, videos, and text messages
- Records of all internet activities
- Geo-location and fencing
Compatibility
- Windows
- iPhone and macOS
- Android
FlexiSpy
It’s software to monitor your devices, no matter where you are. The Flexispy phone monitoring software helps you to track all contact, user online activities, messages, etc. It has more tracking characteristics than any other competitive product, which is wholly justified. This app has the function of spying on somebody’s Line VoIP conversations. So, you can listen to their conversations when someone calls the target device.
Features
- Track MMS and Texts & emails
- Spy on VoIP (Voice over Internet Protocol)calls mobile phone calls and keeps a call log record.
- Position of GPS tracking
- Spy on all the phone’s IM (Instant Messaging) application
Compatibility
- Android
- iOS Apple
- Windows
- macOS
ClevGuard/ KidsGuard
It’s also one of the critical software that monitors the target devices. ClevGuard/ KidsGuard is specially designed for the surveillance of kids. Through this application, you can control any form of data, including GPS. This helps you to monitor anybody’s real-time location and also the messages.
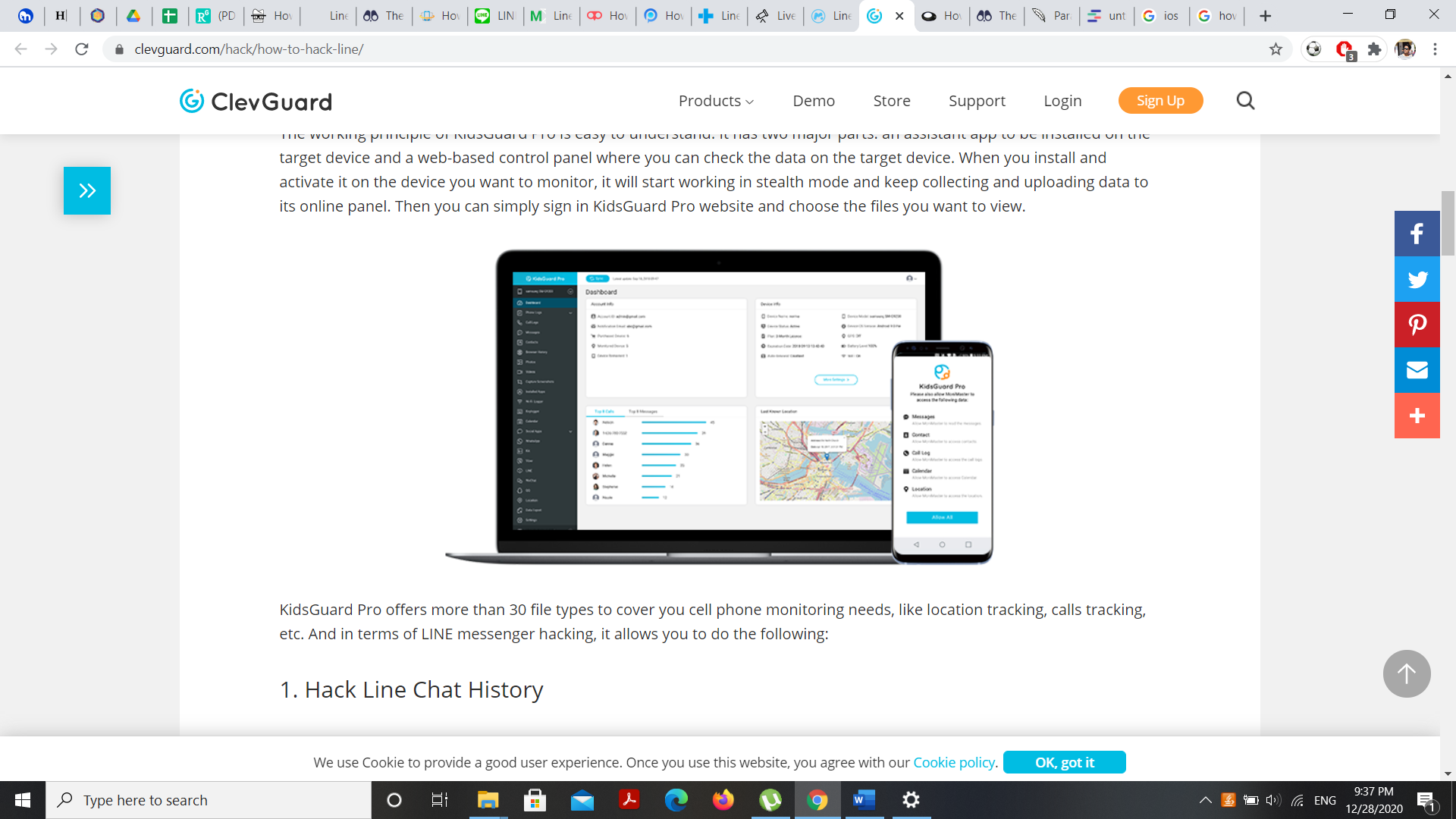
Features
- Check Line Screen Activities
- View and Analyze call log
- Track all installed applications, images, browser activity, etc
- GPS and SMS location tracking
- Hack Line Messages
Compatibility
- Windows OS
- iOS
- Android
- macOS
Spyzie
It’s a straightforward and user-friendly platform for account hacking. This application provides an excellent line tracking option. Spyzie intercepts all text messages directly without the knowledge of the user. It has no advanced features, including streaming live cameras or listening to the user conversation in real-time.

Features
- Operates in stealth mode
- Review the call log
- Track text messages and GPS location
- Spy all messaging application
- Monitor all applications, galleries, Note, and reminders loaded on your phone
Compatibility
- Android
- iOS
Spy Phone
Would you like to hack line messages? Spy Phone is reliable software to monitor the target device. Once you download this app, it begins to upload data from line software to a remote website.
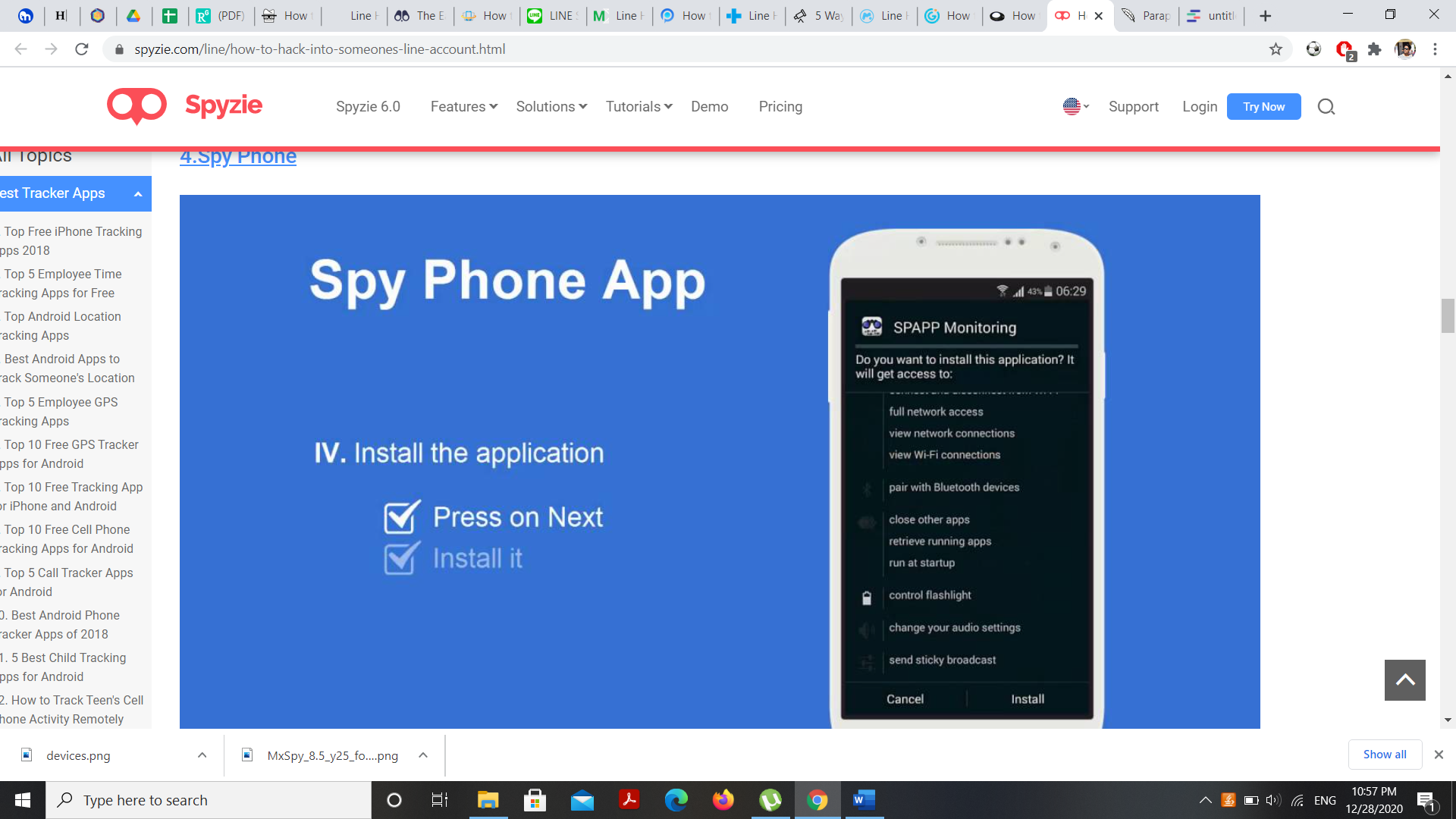 Features
Features
- Can read delete messages.
- Remotely access videos and photos
- Track the spied phone GPS location
- Check internet activities
- Records MMS and SMS of all messaging app
Compatibility
- Android
- iOS
- Both OS
Read More: How to install a spy apps without a target phone?
How does it work?
1: The first thing you have to do is register your account. Once you insert your email and passwords, your login credentials will be mailed.
2: After completing your registration, you need to have detailed information on the device you want to hack.
3: To allow the installation of an application, you need to go to the Developer Option because it doesn’t allow users to download unverified apps.
4: Now, log in with the credentials you created earlier.
5: After installation and login, and choosing the subscription plan, you will have your dashboard or control panel. Now you can monitor the target device
6: The tracking on your computer must be activated. You can now uninstall and leave the software on the target screen. The software will continue to run continuously and hack into a line account.
7: At last, you can spy line messages on target devices in stealth mode.
Ways to protect Line Messages from hacking
- End-to-End Encryption
End-to-end encryption ensures that the encryption of messages on one device can only be decrypted by the device it is sent to. You can encrypt the line message also. If someone accesses your line account, they will not check your message because you need to insert an exceptional recovery encrypted code. This is the most trusted way to prevent line message hacking.
- Two-factor Authentication
It’s a security method that needs two-factor authentication. You can update your account to two-factor authentication, Which allows the user to protect from someone using your account. It’s a two-way login. First, you need to insert the password and verification code that the system has sent to your mobile device. If a hacker accesses the account, you will be notified that your account is being used from another device.
- Updates to the app
It is very important to update the line application. Since the Line application frequently improves its security measures, you can keep your account safe by updating it.
Always use the latest version.
- Keep your registration information up-to-date.
If you change your mobile number, you have to update the number details you have registered on the Line app.
If someone else uses your previously used phone number and they use that number to create a line account, your account of the Line app will become unavailable.
And it’s because the Line app allows only one account per cell number. So, please keep it safe.
- Set a secure account and beware of hacking
Create a strong password by using combination characters of lowercase and uppercase. Also, don’t share your passwords with anyone else. If you do so, then they can hack your Line account without. Don’t use simple passwords that anyone can guess, such as your birthdate, first name, address, and phone number.
In addition, be careful about phone hacking. Don’t click on any suspicious links, be aware of phishing links. Don’t get tricked by fake emails and messages.
Conclusion
Therefore, third parties free software has made people’s lives more convenient. With the help of each software, you can hack line messages. You can also enjoy its best features. Although hacking is an illegal offense, Ethical hacking is a legitimate process to hack or spy on someone’s account. We have to be within consent boundaries to hack line messages or accounts.
Read More: The positive side of spying technology



 WhatsApp Spy
WhatsApp Spy Facebook & Messenger Spy
Facebook & Messenger Spy Viber Spy
Viber Spy Instagram Spy
Instagram Spy Skype Spy
Skype Spy TikTok Spy
TikTok Spy Telegram Spy
Telegram Spy LinkedIn Spy
LinkedIn Spy Twitter Spy
Twitter Spy Youtube Spy
Youtube Spy Photo Spy
Photo Spy Video Spy
Video Spy Calls and Contacts Tracking
Calls and Contacts Tracking SMS & IM Chats
SMS & IM Chats Voice Capture
Voice Capture Image Capture
Image Capture Video Record
Video Record